_
Why use an NDR solution ?

According to IBM Security, on average worldwide, an intrusion is detected 212 days later. In France, large groups are better equipped and better trained than SMEs and SMIs. Thus this period drops to 35 days, according to Wavestone. This is still a considerable period of time, during which a cyber attacker explores the company’s network to recover all its critical data.
This is where the need for a Network Detection & Response solution comes in, to detect the attack before it’s too late.
Let’s take a closer look.
An NDR solution, an essential safety feature
Network Detection and Response (NDR) is a cybersecurity solution that detects all suspicious events on a company’s internal network. Most assets are connected to the network – wireless or wired devices, endpoints or servers, applications, users, etc. And if there is one important thing to know about network traffic, it is that it does not lie.
In the face of increasingly sophisticated cyber attacks, NDR solutions are becoming a necessary tool for continuous network monitoring. There is a good reason why the market for NDR solutions is growing rapidly (23% annual growth).
Unlike traditional signature-based prevention security solutions, the NDR solution goes one step further. By leveraging Artificial Intelligence, Behavioural Analysis and Threat Intelligence, it enables the detection of zero-day attacks, so-called unknown attacks, which are impossible to detect by signature. This is the case with the CUSTOCY solution.
An NDR solution will target all the actions that the cyber attacker will take to access the company’s critical data.
A complementary solution to your cyber defence arsenal
An NDR solution is an essential component in securing an IT infrastructure, recognised by the main players in cybersecurity, including GARTNER.
On the cybersecurity market, we find, among others
- EDR (Endpoint Detection and Response), which offers monitoring of endpoints and the interactions between them.
- SIEM (Security Information and Event Management), which collects event log information from other systems and correlates data from different sources.
- The NDR, which will have a detailed view of the exchanges between the network equipment. A solution that detects elements inaccessible to other tools.
Together, these three pillars provide global visibility of security threats in the enterprise IT environment.
A solution to detect obfuscated activity
Artificial Intelligence in an NDR solution such as CUSTOCY provides strong detection capabilities and a unique perspective on behaviour that is undetectable by other tools.
Signature-based solutions typically use indicators of compromise (IOCs) such as IP addresses, specific protocol usage or anomalies in privileged user account activity. Their rules can be learned and overcome by adversaries who adapt their approach to each target.
AI-based detection, on the other hand, constantly learns the normal behaviour of a network as well as the behaviour associated with malicious activity. An adversary seeking to adapt its strategy to AI-based detection would need to possess a unique knowledge of both the AI system and the network it is protecting: a nearly impossible task.
Artificial Intelligence can therefore detect the most sophisticated and persistent attacks before impact with formidable efficiency and accuracy. Thus avoiding the management of collateral damage.
CUSTOCY provides an intuitive NDR solution
CUSTOCY has been developed in-house, by renowned cybersecurity experts and data scientists with the following objective: to have the best AI detection on the market.
Beyond efficiency, CUSTOCY is designed to relieve cybersecurity analysts who defend digital assets of companies every day. Today, it is difficult for a single individual to correlate all the elements that occur on the network. They are subjected to an avalanche of inconsequential alerts and feel overwhelmed by the sheer volume and sophistication of data they monitor.
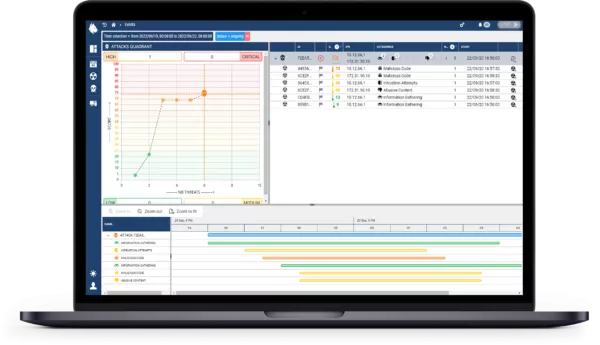
The contribution of artificial intelligence in CUSTOCY is a real support to analysts because it alerts them only in case of significant traces of attacks, ensuring 88 times less false positives.
In addition, the intuitive interface is quick and easy to use and offers a synthetic view of threats with the possibility of replaying them and understanding why the AI has triggered alerts. Everything is transparent and IT security management is simplified.
Curious to discover this new NDR solution? Book your demo slot, it’s free! 👇HERE.

